Kryptera halts use of stolen files.
Automatic encryption or decryption of files, including stored within complex directory chains
Kryptera is a tool that is used to automate encryption and decryption of files.
- One to many files can be automately encrypted or decrypted by simply transferring files, or complete directory chains, to the Kryptera server input queue.
- Kryptera first checks if a file signature exists.
- If so it validates the signature.
- If the signature proves it has been encrypted then the file is passed to a thread to decrypt.
- If the signature proves it has is an encrypted command file, then is passed to a thread to process.
- Otherwise it is passed to a thread to encrypt.
Our products use 384-bit cryptographic-quality random keys.
- Kryptera Enterprise:
- Quantum-secure encryption.
- Works on embedded to server hardware plus cloud containers.
- Fully utilizes CPU cores.
- Builds and configuration can be highly customized for clients.
- Kryptera Mirage:
- Quantum-secure encryption.
- Far faster file processing than Enterprise.
- Fully utilizes CPU cores.
- Best used for situations where extreme speed is needed.
- Kryptera Sibylline:
- Quantum-secure encryption.
- Used to automate encryption and decryption.
- Builds are synchronized for embedded and desktop use.
- Designed for anonymous paired encryption and decryption.
- Used to protect X-Ray scanned images.
Our products automate encryption of individual files and one to many files within complex directory chains.
- When used to encrypt directory chains.
- Each file within the chain is randomly encrypted.
- Each file cannot be decrypted without use of the same hardware security module (HSM).
- When an encrypted file is stolen it is impossible to decrypt without priviledged access to the same HSM.
- Advanced techniques are used to only process files and directory chains that have been fully written.
- Irrepairable file and directory chain damage can occur if writes are not completed before processing begins.
Enhanced HSM
A hardware security module (HSM) is a dedicated networked server that is primarily used to handle encryption and decryption of files.
High-speed file security is available in a secure environment protected from most network access.
We produce high-quality enterprise-class HSM products.
Our products are designed for IT departments to enforce risk reduction of leaks if private files are stolen.
Common HSM Features
Kryptera product lines share common features with other HSM products:
- Dedicated turnkey networked server to handle cryptographic file processing.
- Cryptographic-quality random number generation.
Unique Kryptera Features
Our product lines have unique features not found in other HSM products:
-
Automates:
- Encryption and decryption of files, including folders containing files.
- Processing of many files at the same time using all CPU cores.
- Files and folders are transferred to an input queue for processing.
- Processed files and folders are transferred from an output queue.
- Multiple input and output queues can be supported.
- Quickly and easily deployed and used.
-
Provides Control:
- File security controlled by IT departments.
- No need to custom develop software using an HSM API.
- Network scripts and software can help to automate file and directory transfers.
- Greaty simplifies private key management.
- Fast recovery after destruction or loss of HSM.
-
High speed software algorithms:
- Not dependent on underlying CPU.
-
Has been deployed on:
- Lower-speed embedded hardware.
- Variable-speed containers.
- High-speed multi-CPU servers.
- Features can be customized:
- Input and output queues securely shared in Local Area Network (LAN)
- For Example:
- Mount the input queue and the output queue.
- Use input queue mount to write backups of the database system.
- The HSM automatically encrypts the backup then moves it to the output queue.
- The mounted output queue is used by a process to move the encrypted backup into long term storage on cloud storage, NAS, tape, etc.
- Hierarchical HSMs: Local Area Network (LAN) or Wide Area Network (WAN)
- Example: Management HSM, and divisional HSMs for Finance and Sales.
- Finance HSM encrypts files that cannot be decrypted by other divisions.
- Sales HSM encrypts files that cannot be decrypted by other divisions.
- Management HSM where only Management can decrypt their files.
- Management HSM set to decrypt files provided by Finance and Sales.
- Secure LAN group
- Example: Management and divisions share use of a single HSM in a LAN
- Secure WAN group
- Remote groups each use their own HSM yet can share encrypted files in the group that can be decrypted by any secure group member.
- Secure WAN/LAN group
- Remote groups each use their own HSM in a LAN configuration yet can share encrypted files in the group that can be decrypted by any secure group member.
Invented and created from the ground up
Our products were created from the ground up.
- We did not use any other product as a model to create our products.
- We knew we had to provide a straightforward approach.
- An approach for IT administers to stop the leaks of stolen private files.
- Our products are designed to be quickly and easily utilized by IT departments.
- Utilized without need for custom software development using a PKCS #11-compliant API.
- Our products have no reliance on third party frameworks, APIs or libraries.
- This maximizes security and guarantees long term use.
- We do not provide access through an application programming interface (API).
- We took this lengthy, costly and difficult approach to reach the highest level of security with the fastest level of performance.
- We took our time to create, test, refine and enhance our products, before we completely reviewed and refactored our entire source code base.
- Everything we have done has made our products more secure, stable, faster and easier to use.
- This is known as a substitution–permutation network (SP-network or SPN).
- The current key is mutated again.
- The mutated key is expanded into a random key pool.
- 16-bit key objects are drawn from the key pool and used to encrypt each plaintext object.
- Each plaintext and cyphertext object can range in value from 0 to 65,535.
- On key pool exhaustion the current key is mutated then expanded into the key pool.
- This cycle repeats until a file has been fully encrypted.
- Random key objects are used to randomly select a unique substitution table.
- Our algorithms makes use of a total of 2,147,418,112 highly unique substitution tables.
- It is possible to generate a total of 7.878034245 E+287188 16-bit substitution tables.
- This is the factorial of 65536.
- A factorial determines how many ways 'objects' can be uniquely organized.
- For example, Charlie, Linus, Lucy and Sally can be arranged in 24 unique ways.
- The factorial of 4 is 24, which is calculated: 1 x 2 x 3 x 4.
- A 16-bit value is extracted from a randomly selected randomly organized substitution table.
- The extracted value corresponds to the position of the plaintext value in the substitution table.
- The extracted value is randomly changed by performing an exclusive disjunction using another random key pool object.
- One to many rounds of this cycle is supported.
- The result is a cyphertext value that is saved to the encrypted file.
- Each encrypted file leads with a multi-level encrypted header.
Our encryption process
Our products encrypt plaintext files 16-bits at a time.
Our cryptographic algorithms rest on a solid foundation of object substitution and permutation.
Our algorithms make use of cryptographic-quality random 384-bit symmetric keys.
Kryptera RNG Test01 Crush Test Results
The keys are randomly drawn from several large encrypted containers of generated cryptographic-quality random objects.
The container and position within that container are both randomly selected.
A key is drawn from the selected container, decrypted then is randomly changed (mutated).
The processing cycle begins.
The result is a quantum-secure encrypted file that can only be decrypted using the same server.
Theft of private files by trusted insiders
It is almost impossible to stop the theft of private files by trusted insiders
It may be possible, though often unfeasible, to stop file theft by attackers gaining access to computers, mobile devices, networks, servers, and cloud storage, flawed operating systems and software applications, insecure backups, and back doors in hardware and software.
Private files have been stolen, are being stolen, and will be stolen.
Leaks and improper use of private files occur every day.
Automated Risk Management
Kryptera HSMs are risk management solutions used to minimize the risk of private file leaks.
Kryptera HSMs are a secure turnkey solution that embraces server-side file processing.
Processing to automate encryption and decryption of files including files within complex directory chains.
Full automation is possible through scripting, server configuration, and use within a private network.
Kryptera HSMs provide high-speed mass processing and queuing of files and directories.
Kryptera HSMs are autonomous. They do not communicate with external networks, do not require external private key management, and manage private keys internally in a secure and unique manner.
Kryptera HSMs are inventive and disruptive.
Kryptera makes complex simple.
The reality that most people and organizations face today
This may prove difficult to read, but it's the truth.
After that we'll provide details about our HSM solutions that will permanently alter your reality for the better.
Our solutions are inventive.
We created completely new hardware security module solutions.
A new approach with a new design using all new proven technology to make it all come together.
Our solutions were designed to simplify encryption and decryption of files.
Simplify to remove obstructions that prevent organizations from protecting their most valuable assets.
Our products provide IT departments with control over file security rather than rely on provision of a PKCS #11-compliant API.
- Most organization fail to encrypt digital assets because of the time, cost and hassle of doing it right.
- Some naive users relying on easily broken passwords and passphrases to simplify decryption.
- Other users recklessly storing their passwords and passphrases in documents, on paper, in post it notes, in source code, and in their memory.
- Some users fleeing to what they perceive as the safety in the Cloud, but not encrypting the files they upload, nor securing storage buckets or search technology used to access them.
Threat of Insider Crimes
The Growing Threat of Insider Crimes

We’re facing a very serious crisis today that is not going away
The problem is cybercrime, and more specifically, the rapid growth of insider breaches.
The problem is getting worse, not better, with global losses approaching $3 trillion a year.
A key to the problem lies with current forms of encryption that require users to retain and manage passwords, passphrases and private keys.
Some organizations are now managing millions of encryption keys.
This has resulted in:
- delay encrypting their private files;
- manually handle multiple passwords, passphrases or private keys to encrypt and decrypt files, or
- use inefficient private key management systems to encrypt and decrypt files.
Addressing the problem
Kryptera HSMs Address the Problem Head-on
Kryptera HSMs come to the rescue, with a breakthrough approach to encryption of private files.
Kryptera's high speed mass encryption uses a unique method of internal key management.
Kryptera supports processing of many files, even within complex directory chains, at the very same time.
So no more excuses, no more hassles, no more reason for organizations to:
So why rely on obsolete encryption methods?
Kryptera has a brand new key that can help you stop leaks of private files and manage the insider threat crisis.
How Bad is the Insider Threat?
We have created an ever growing list of articles that relate to security risks.
This list will confirm the validity of claims we make that relates to risks.
Please share this list with subject matter experts within your organization to determine risk levels and exposure.
- State Actors
- Criminal organizations
- Current and future competitors
- Activist groups or disgruntled people
Deception

Deception
Criminal employees may work alone or report to:
Breaches

Insider Breaches
Insider breaches have been increasing year after year. Today, over 60% of reported losses now come from within. Most losses are not reported.
It is simply too easy to steal from inside without being caught. The main culprits are trusted insiders, often unvetted by HR. Even ordinary employees can cause serious security breaches.
Motivations

Motivations for Inside Theft
| Debts | Obligations | Legal Issues | Blackmail |
| Addiction | Illness | Beliefs | Hatred |
| Greed | Control | Justice | Vengeance |
| Jealousy | Envy | Pride | Gullibility |
| Fear of suffering | Opportunity | Grudges | False news |
Rogue Employees

Employers Make it Easy for Rogue Employees
New employees are often provided with a computer that connects to internal and external networks.
Many employees are given access to email, private storage areas, shared resources, an Intranet site, and remote VPN access.
Smartphones may be provided, or the use of personal smartphones encouraged.
Privileged Access

Criminal Employees May Have Privileged Access
Organizations rarely monitor access to R&D, database administration, network administration, and critical roles in IT, support, finance, sales and marketing.
Criminals can work at these levels and be trusted, can operate beneath the radar and do things that can prove impossible to detect or stop.
They steal confidential files with impunity, insert back-doors, and destroy anything they want.
Dark Web

Anyone Can Use The Darknet (aka Dark Web)
Employees familiar with the Darknet can unleash destructive events.
Providers of malware, ransomware and DDoS attacks found in the Darknet will attack an organization at low cost. Providers share revenue or pay for information to simplify attacks. Buyers will pay for stolen files and private information. The Darknet is available through the Internet, and accessed using the Tor network.
- Social Security number: $1
- Credit or debit card (credit cards are more popular): $5-$110
- With CVV number: $5
- With bank info: $15
- Fullz info: $30
- Note: Fullz info is a bundle of information that includes a "full" package for fraudsters: name, SSN, birth date, account numbers and other data that make them desirable since they can often do a lot of immediate damage.
- Online payment services login info (e.g. Paypal): $20-$200
- Loyalty accounts: $20
- Subscription services: $1-$10
- Diplomas: $100-$400
- Driver's license: $20
- Passports (US): $1000-$2000
- Medical records: $1-$1000*
- *Depends on how complete they are as well as if its a single record or an entire database
- General non-Financial Institution logins: $1
Theft for profit
How Much Your Personal Information Is Selling for on the Dark Web
Here are the 10 most common pieces of information sold on the dark web and the general range of what they're worth—or rather can sell for:
Attacks
Motivations for Attacks
Attacks are levied in retaliation for perceived grievances, to bring down a competitor, silence opposition, stifle contrary information, make money or simply to cause chaos.
Attacks can create high-paying work for people associated with an attacked organization. An internal criminal can leverage internal chaos to steal and transport private files and information.
- Copy original files to internal storage
- Create hidden files under all operating systems
- Create invisible files using Windows NTFS Alternate Data Streams (ADS)
- Write to unused disk sectors on internal storage
- Copy to a RAM disk
- Write to a non-monitored storage partition
- Copy to USB media such as a USB stick, USB drive, SD card, or SSD, or copy to a USB device
File Movement

Access, Store and Transport Files
To steal digital data requires access to files and information, temporary storage to house stolen files, and methods of transport for stolen files.
Temporary Storage of Stolen Files
Intelligent criminals can easily:
- Through a direct Internet connection
- Connected through a cell phone WiFi hot spot
- Through a WiFi router to storage media, or to another connected computer
- Through a Bluetooth connection to another computer or smartphone
- Through a wired connection with another computer
- On USB, SD or SSD media
Transport
Transporting Stolen Files
Criminals can copy or steal files:
- Power down the target computer
- Remove the internal storage
- Insert the internal storage into a USB storage dock or USB storage casing
- Power up another computer, and log in using an administrator-level account
- Connect the USB storage to the computer
- Copy files and directories from the USB storage to other media or transport to a remote server or Cloud
Access

Gaining Full Access
To gain full access, criminals can:
This is an effective way to gain full access to drive contents without an account or password
Encrypted Storage
Encrypted Storage
Organizations can also encrypt internal storage to prevent plaintext copying to USB storage. Encrypted storage is only secure after it has been powered down.
Hiding

Avoiding Detection
To avoid detection, insider criminals can transport stolen files from original sources, leaving fewer traces behind.
They can clean traces of their activity to prevent detection, and securely erase files after transport.
By defragmenting internal storage, they can overwrite sectors previously used by stolen files.
Traces

Traces Left Behind
Insider criminals can leave traces behind. Shared network logs should be reviewed to check if employees are copying too many files.
Traces will be left behind if internal storage placed is in a USB case is accessed on a Windows or Macintosh computer. This is prevented by using a Unix or Linux computer, or by using a USB case that includes a read-only switch to prevent writes.
- Publically exposing Elasticsearch Server poses a major security risk
- Employees of Cloud providers may have criminal motives
- Cloud file storage is regularly reused and may prove insecure
- Cloud space breaches can leak original files
- Cloud outages prevent file access
- Cloud providers can delete space on non-payment
- Some cloud providers work closely with state actors
- Cloud backups may be insecure
- Criminals can leverage Cloud use into large scale theft
- Sharing or insecurely storing credentials can compromise Cloud accounts
Improper Cloud Use
Unauthorized Cloud Storage
It is common for employees to set up Cloud space without authorization from the IT department.
Once set up, original private files can be directly transferred into Cloud space.
This can lead to long term problems for the organization. When original private files are present in Cloud space, the risk is high that security will become an issue.

Storm Clouds
Smartphones
Criminal Use of Smartphones
Smartphones are major security risks.
Most smartphone applications are highly invasive, and malware infection is extremely common.
Rogue applications can capture keystrokes, audio, video, still images, screen captures, web activity, telephone calls, and most other forms of communications.
Smartphones Are Insecure
Smartphones can be connected to computers using a cable, WiFi, Bluetooth, and Near Field Communication (NFC).
SIM cards can be changed to communicate over alternate carrier networks.
Methods abound to transport stolen files and information using smartphones.
Trusted Risk
Trusted Technology Is Risky
Technology provided by Amazon, Apple, Cisco, Facebook, Google, Microsoft, Samsung and others present security and privacy risks to users.
Each have created technology that records and retains private conversations and actions.
Some retain video, audio, and telephone conversations. Most retain location and other private information.
Some permit staff to review stolen recordings, where another relies on staff to transcribe stolen recordings.
Organizations should avoid relying on technology that creates internal security issues.
Indifference
Criminals Do Not Care
It’s hard to accept that people you trust and respect, that you work with and spend time with, are criminals.
Criminals who steal and leak private information do not care about the destruction they cause.

Kryptera Addresses The Insider Threat Crisis
Kryptera Technologies has created the Enterprise and Mirage product lines.
Both products share features such as manual or automated high speed encryption and decryption of many files at the same time with internal private key management.
- Enterprise is a general purpose product line that can be customized for clients.
- Mirage is far faster than Enterprise, and best used for special situations where extreme speed is needed.
Protection
How Kryptera Can Protect Organizations
File encryption, with regularly scheduled encrypted backups, are the major ways to defeat leaks of stolen files, and associated loss.
Kryptera technology is directed to these ends.
We're pessimistic.
Dedicated thieves will always find ways to steal and transport what they want and little can be done to stop it. But Kryptera offers a simple solution to stopping leaks:
- Preventing use after theft.
- Make stolen files useless to thieves.
With Kryptera in operation, there is no way thieves can decrypt a file without access to the same Kryptera server, or the same secure group of Kryptera servers, used to encrypt the file.
Simplying Complexity
Why Avoid Encryption When Kryptera Makes it Simple?
Kryptera products are designed to simplify encryption/decryption.
We make complex simple. And simplicity removes any reasons to avoid encryption of valuable private files.
Each product is provided on a turnkey network server that has been securely customized for client use.
Kryptera servers efficiently reduce the risk of leaks through high-speed mass encryption of many files and directories of files at the same time.
Configurations
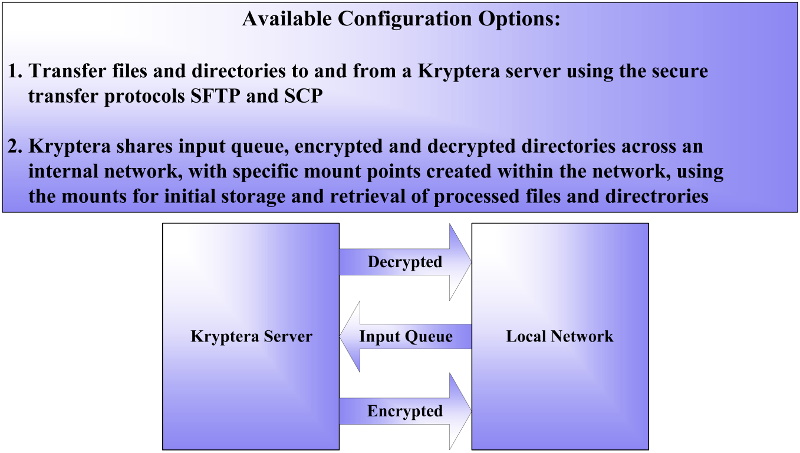
About Enterprise and Mirage
Private key management is central to Kryptera design and is internally handled in a highly secure manner.
Our design allows for queuing up of an unlimited number of files and directories for processing.
Files are randomly and securely encrypted.
Encrypted files normally cannot be decrypted on a different Kryptera server.
Two Kryptera features negate this limitation
Kryptera Encrypted File Sharing (EFS)
- Files encrypted on any EFS server in a secure group can be decrypted on any EFS server in the same group.
- EFS servers can be located in any country that permits use of high-strength encryption.
Kryptera Hierarchy
- Isolated departmental secure groups are created, each using a unique Kryptera server.
- One or more managerial secure groups are created that can also decrypt files from one or more isolated secure groups.
Kryptera Encrypted File Sharing
The EFS feature can be used within many high-security scenarios.
One scenario can correct a widespread security fault where original private files have been directly stored in Cloud space and are subject to leaks on Cloud breach.
Correcting a Cloud Fault Using EFS
Using two Encrypted File Sharing (EFS) servers will correct this problem:
A virtualized EFS server is hosted in Cloud application space,
and used to encrypt files, and directories of files, in the Cloud.
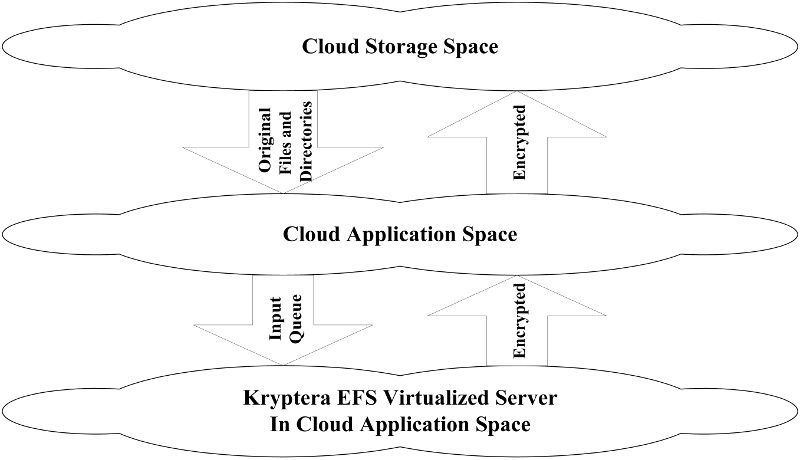
A turnkey EFS server is hosted in a client’s private
network operation centre or another secure location.
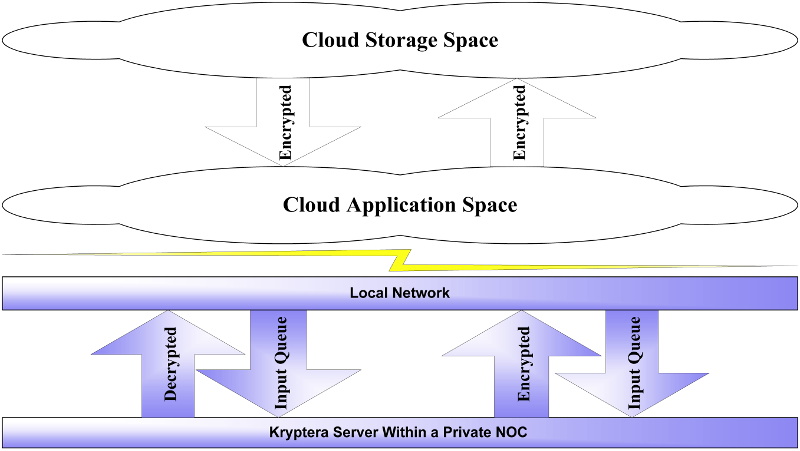
Security in the Cloud
A Kryptera server hosted in a private network is used to decrypt files brought down from Cloud space, and encrypt files before transport into Cloud space.
This design minimizes risks of Cloud breaches leading to leaks.
The EFS Risk Reduction Cycle
Original files, including complex directories, that are stored in Cloud space will be mass-encrypted using the virtualized EFS server.
Available cores and memory, and speed of storage on the virtualized EFS server determine how quickly files can be encrypted.
Automated processing can occur 24/7.
As processing completes, original files and directories can be replaceed with the encrypted versions.
The virtualized Kryptera server is then destroyed after all files and directories have been encrypted.
Kryptera Hierarchy
This feature enables creation of a hierarchy of Kryptera servers.
For example, an administrator can create one to many departmental servers where each unique server is used to encrypt files that cannot be decrypted by other departments.
One to many managerial servers can then be set up to decrypt encrypted files from one to all departmental servers.
Managerial servers can encrypt files that cannot be decrypted by any other server within the organization, unless the hierarchy allows it.
Automating Encryption of Backups
Kryptera servers can be configured to share out queue directories within an internal network.
Sharing of queues can automate encryption of archival backups prior to storage.
The archival backup would be written to a mounted input queue. The archive is encrypted then moved to a shared output queue directory used as a source for final storage to tape, NAS or cloud.
Kryptera Enterprise Server
The Enterprise product line is highly customizable and designed for general purpose use.
The Enterprise code base can be used to create products that will operate on large capacity servers and computers down to extremely small computers and devices.
Kryptera Mirage Server
Mirage was refined for maximum speed and designed for special use.
While both product lines encrypt and decrypt files of any size, Mirage is three times faster than Enterprise when tested on identical hardware.
Mirage is best for critical processes that require real time encryption such as post-production movies, CCTV feeds, and database backups.
Kryptera Sibylline
Sibylline was created using the Kryptera code base for a special project.
We are retricted by a Non-Disclosure Agreement (NDA) on what information we can provide.
Sibylline was used on a Flat Panel Detector that is used for X-Ray imaging.
Embedded firmware on each FPD utilizes Sibylline to encrypt X-Ray scanned images before they are written to storage media.
The embedded hardware does not provide support for AES-NI at a hardware level.
AES software processing is extremely slow on the embedded hardware due to the complexity of the algorithm.
Sibylline processing is fast on the embedded hardware.
Sibylline was incorporated into an associated Windows 64-bit Software Development Kit (SDK).
The SDK is used to decrypt images provided by the FPD.
Sibylline was designed for anonomous encryption and decryption of images.
The FPD has no knowledge of the computer (SDK) used to decrypt images.
The SDK has no knowledge of the FPD used to encrypt images.
Encrypted images cannot be decrypted without use of the SDK.
Internal Security Consulting

We have solid experience directly relating to the theft of private data and information.
We have reconfigured computers and servers to bypass security, restrictions and monitoring, and have cleared all traces of activity. We have also developed software that relates to NTFS ADS and direct sector writes.
We can help you to reduce internal risks, and isolate related problems.
Copyright © Kryptera
